How to Secure and Verify GitLab Webhooks with Hookdeck
Webhook security and verification are critical components in assuring the security and integrity of your data transmission. GitLab, a web-based Git repository manager, allows developers to receive webhook notifications when specified events occur, such as a push to a repository or a new release. However, if these webhooks are not adequately secured, they can be vulnerable to security threats such as fraud, replay attacks, man-in-the-middle attacks, and unauthorized access. Learn more about webhook security here. For a comprehensive overview, see our guide to GitLab webhooks features and best practices.
As a developer, dealing with each platform's webhook security implementation often leads to a lot of maintenance issues, especially having to add and manage new providers. Hookdeck removes this layer of complexity by letting you manage all of them using Source Verification, and then you only have to implement Hookdeck's signature verification on your server(s).
This article shows you how to set up and configure your GitLab webhooks manually and with Hookdeck. By the end of the article, you will have a comprehensive understanding of how Hookdeck can help secure your GitLab webhooks and protect your codebase and business from potential security threats.
How to manually secure GitLab webhooks
To manually secure your GitLab webhooks, you are required to follow these steps:
- Create a new webhook integration on GitLab with SSL enabled.
- Select the events to listen to and generate a secret token for the webhook.
- In your webhook receiver code, check for the presence of the
X-Gitlab-Tokenheader. - Compare the token value in the header to the secret token you generated in GitLab. Use a timing-safe comparison (such as
timingSafeEqual) to prevent timing attacks. - If the tokens match, process the webhook. If they don't match, reject the webhook.
Note that GitLab uses a direct token comparison via the
X-Gitlab-Tokenheader rather than HMAC-based payload signing (as used by platforms like GitHub). The secret token is sent as-is in the header over TLS, so always ensure SSL verification is enabled.
Learn more about securing GitLab webhooks here.
Verifying GitLab webhooks manually using the steps provided offers a secure solution for webhook validation. However, it also presents several challenges, like difficulties in securely managing and storing the secret token, complexity, and time wastage as far as implementation and maintenance.
GitLab also includes several useful headers with each webhook request that can help improve reliability:
X-Gitlab-Event: Identifies the type of event (e.g.,Push Hook).X-Gitlab-Webhook-UUID: A unique identifier for the webhook configuration, useful for log correlation and debugging.X-Gitlab-Event-UUID: A unique identifier for each individual webhook delivery.X-Gitlab-Instance: The base URL of the GitLab instance that sent the webhook.Idempotency-Key: A consistent identifier across retries, allowing your receiver to detect and safely ignore duplicate deliveries.
Additionally, GitLab supports custom headers (up to 20 per webhook) for authentication to external services, URL masking to hide sensitive portions of your webhook URL, and admin-level outbound request filtering to restrict webhook destinations by IP or domain.
How to secure and verify GitLab webhooks with Hookdeck
To secure and verify your GitLab webhooks with Hookdeck:
- From your Hookdeck dashboard, create a Hookdeck connection with GitLab as the source and your application as the destination. When creating the source, select GitLab as the source type to automatically tailor configuration options for GitLab webhooks.
- Create a GitLab webhook or select an existing webhook you wish to secure.
- Set the Secret token and enable SSL verification for the webhook, then Add webhook.
- From your Hookdeck dashboard, navigate to Source Verification and select GitLab from the list of platforms.
- Fill in the Secret token as the secret received above and choose the GitLab source connection to secure.
You can select multiple sources and secure them at once.
You now see the GitLab integration at the top of the verification page and the connection showing a green shield on the connection page.
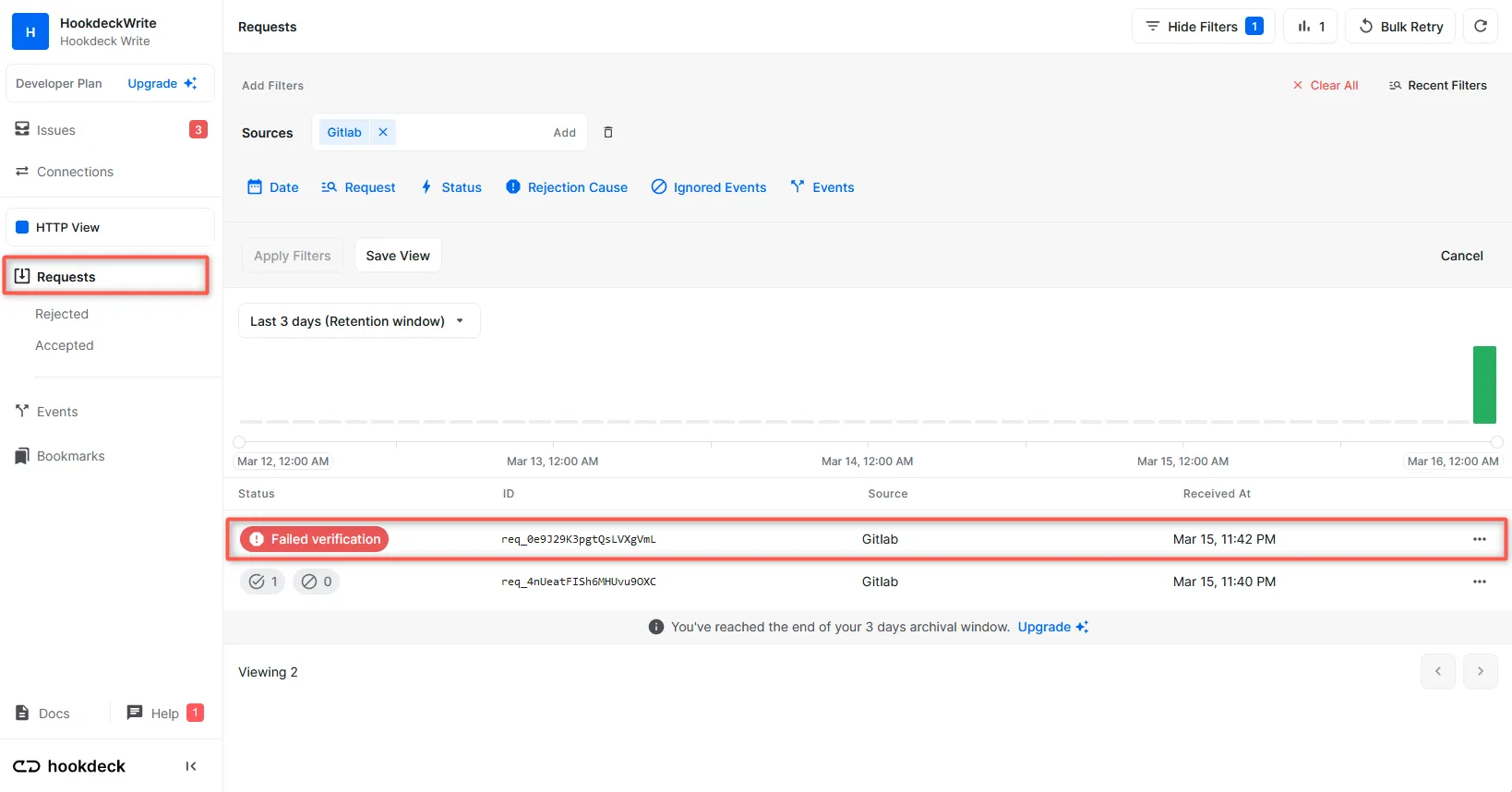
Legitimate requests from GitLab get received successfully with a 200 status code, while any request without the signature is flagged with Failed verification and doesn't make it to your destination.
Hookdeck also adds an
x-hookdeck-verifiedheader (set totrue) to requests forwarded to your destination when the original request has been verified, giving your application an additional signal to confirm authenticity.
Hookdeck can be used to centralize your webhook security and verification, making it easy for you to only sign Hookdeck on your server. See the guide here.
Conclusion
In this article, we have seen why it is important to secure and verify GitLab webhooks, how manual verification can be complicated to handle, and the ease of implementation with Hookdeck.
In conclusion, using Hookdeck simplifies and streamlines the process of verifying GitLab webhooks, making it easier and more secure for developers to integrate quickly. By leveraging Hookdeck's automated verification process, you can be confident that you are accurately receiving and responding to GitLab webhook events without having to manually perform the time-consuming and complex steps involved in manual verification.
