How to Use Hookdeck with Cloudflare Bot Fight Mode
Have you protected your website using Cloudflare Bot Fight Mode? Great! But have you noticed that your Hookdeck webhooks aren’t reaching your server anymore because they’re blocked by Cloudflare? Not so great.
In this post, I’ll guide you through the steps required to make Hookdeck and Cloudflare bot protection work happily together.
Symptoms
When your Hookdeck webhooks are being blocked in this scenario, you will notice your webhooks have been denied by Cloudflare with a 503 error.
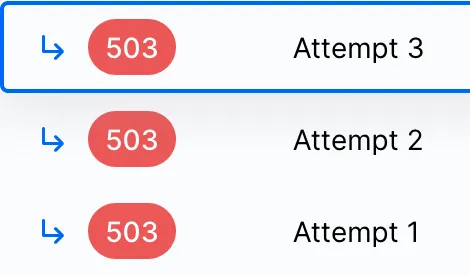
The response body shows up as an HTML page containing the following message in the middle: “DDoS protection by Cloudflare.”

What to do when whitelisting conflicts with autoscaling
To make sure that Cloudflare doesn’t block Hookdeck requests, you need to whitelist Hookdeck’s attempt servers on your Cloudflare site.
Since Hookdeck scales dynamically and we often automatically provision new servers to meet with the demand (sometimes temporarily during peaks, or sometimes permanently), we cannot provide you with a static list of IPs! Or can we?
Enable Hookdeck static IPs on your project
To deal with this problem, we came up with an alternate delivery path for webhooks that you can enable at the project level, and that will use a specific infrastructure to guarantee that your webhooks will be delivered through a static set of IPs.
You can find it in your project settings:
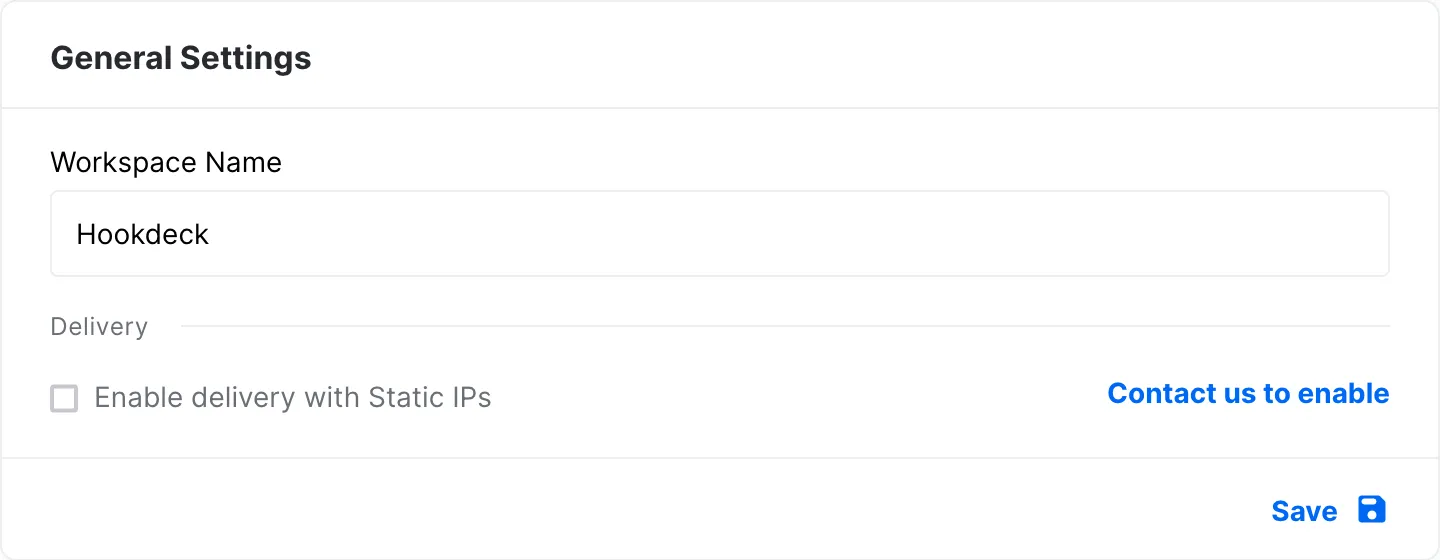
Static IPs is currently a paid-on to your project. You need to contact us to enable static IPs.
Whitelist Hookdeck IPs
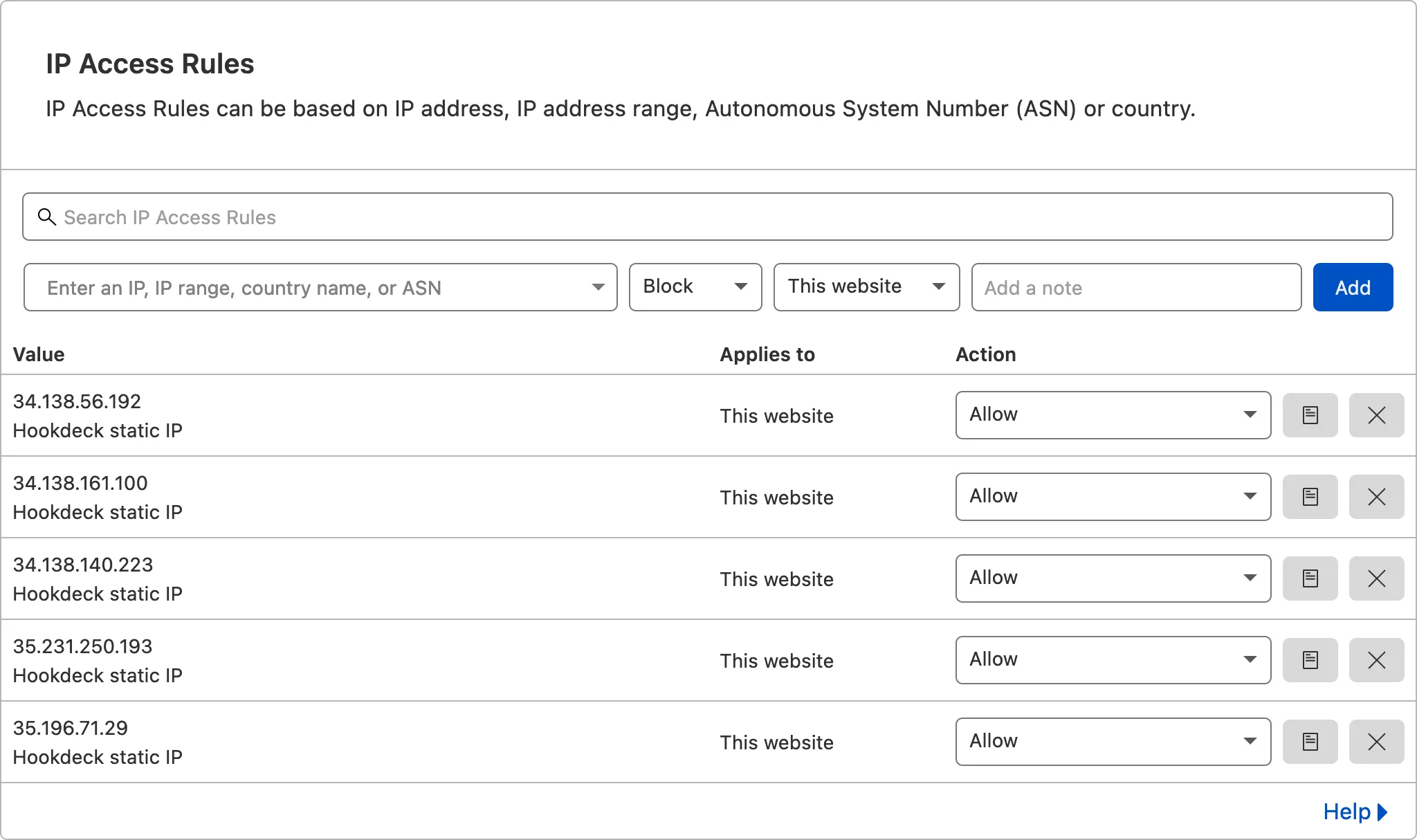
You also need to add the Hookdeck IPs to your Cloudflare whitelist. You’ll find it in the “Security” “WAF” menu.
Here’s the list of IPs we will send webhooks from when static IP is enabled:
35.196.71.29
35.231.250.193
34.138.140.223
34.138.161.100
34.138.56.192
In the end, your Cloudflare IP rules should look like this:
The tradeoff with static IPs
While our ingestion infrastructure is still able to scale dynamically based on the traffic we get, by enabling static IPs on your project we create a potential bottleneck at the delivery level.
While we can still scale the delivery workers as much as we want, the static IP workers are behind a NAT with a fixed 5 outbound IPs. Because of the limit of 64,512 ports per IP, we’re limited to delivering at most 322,560 webhooks in parallel for all of our static IP customers.
We decided that this limit is high enough to give us a significant amount of headroom for the foreseeable future!
When we grow our static IP traffic to a point where we need to add more IPs so as to not run into network issues, we’ll reach out to let you know the new IPs to whitelist.